Element of cyber security is the key to protecting data from online threats. It includes measures like firewalls, encryption, and strong passwords. Without proper security, hackers can steal sensitive information. A strong cyber defense keeps businesses and individuals safe.
Cyber security has several critical elements, from network security to user awareness. Firewalls block unauthorized access, while encryption keeps data unreadable to hackers. Regular updates and strong passwords add extra protection. Want to know the best ways to stay safe online? Let’s explore the key elements of cyber security! 🚀
9 Various elements of cyber security
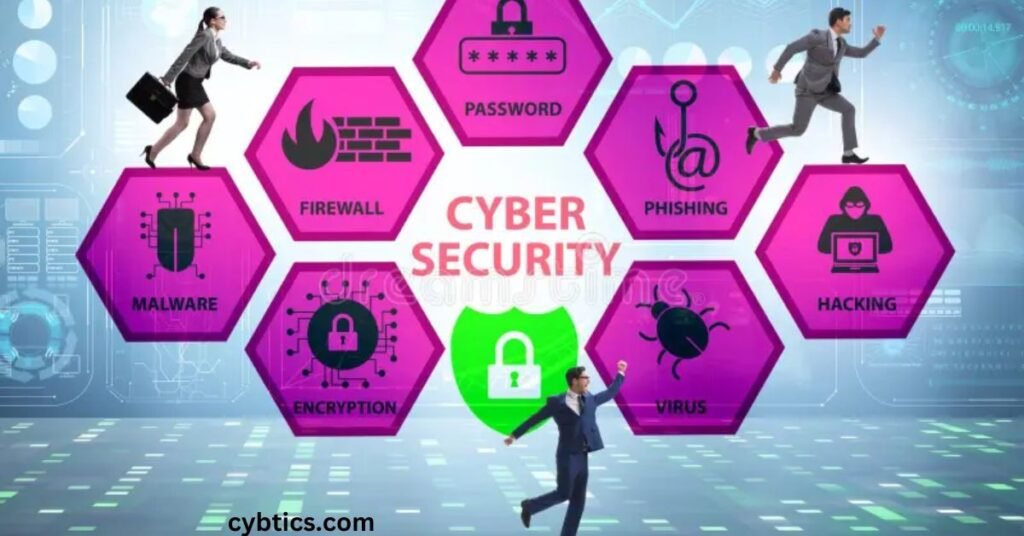
Various elements of cyber security include firewalls, encryption, and strong passwords. They work together to protect data, networks, and systems from cyber threats.
Application Security
Application security protects apps from cyber threats like hacking and malware. It ensures safe and secure software for users.
- Uses firewalls to block unauthorized access
- Encrypts data to keep it safe from hackers
- Regular updates fix security weaknesses
- Strong passwords and authentication add extra protection
Without application security, apps can be easily hacked. Protecting them keeps user data and business information safe.
Also Read: What Is Reconnaissance in Cyber Security? Tools and Techniques Used by Hackers
Information Security
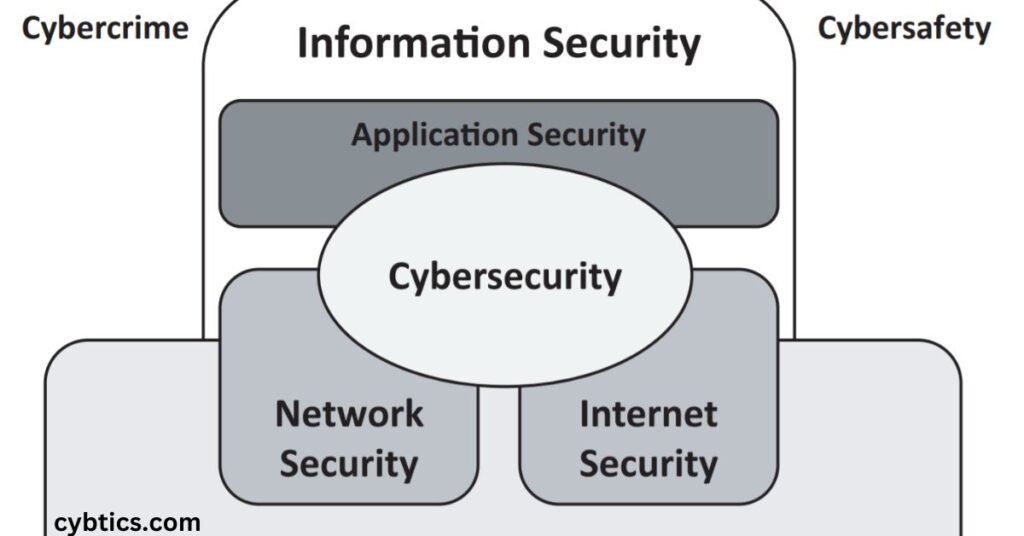
Information security protects data from theft, hacking, and unauthorized access. It keeps personal and business information safe.
- Uses encryption to secure sensitive data
- Firewalls block cyber threats and hackers
- Strong passwords and multi-factor authentication add protection
- Regular updates fix security vulnerabilities
Without information security, data can be stolen or misused. Protecting it ensures privacy and prevents cyber attacks.
Network Security
Network security protects systems from hackers, malware, and unauthorized access. It keeps data safe while traveling across networks.
- Firewalls block harmful traffic and cyber threats
- Encryption secures data during transmission
- Antivirus software detects and removes malware
- Regular updates fix security weaknesses
Without network security, hackers can steal data and disrupt systems. A strong defense ensures safe and reliable connections.
Disaster Recovery Planning

Disaster recovery planning helps restore data and systems after cyberattacks or failures. It ensures businesses can recover quickly and continue operations.
- Backs up important data regularly
- Creates a step-by-step recovery plan
- Tests systems to handle emergencies
- Identifies risks and prepares solutions
Without disaster recovery planning, data loss can be permanent. A solid plan keeps businesses running even after a crisis
Operational Security
Disaster operational security ensures systems stay protected during emergencies. It helps businesses recover safely without data loss.
- Monitors networks for security threats during disasters
- Uses backup systems to keep operations running
- Implements strict access controls for safety
- Regularly tests security measures for effectiveness
- Steps: Identify risks, create a security plan, test systems, and update policies
- Operations: Data backup, access control, threat monitoring, and system recovery
Without disaster operational security, cyber threats can worsen a crisis. A strong plan keeps data safe and businesses running smoothly.
End-user Security

End-user security protects individuals from cyber threats like hacking and phishing. It ensures safe use of devices and online accounts.
- Uses strong passwords and multi-factor authentication
- Avoids suspicious emails and phishing links
- Installs antivirus software for protection
- Updates software regularly to fix security flaws
Without end-user security, personal data can be stolen or misused. Safe online habits help protect accounts and sensitive information.
Prevention
Prevention is the first step in protecting data from cyber threats. It involves using strong passwords, firewalls, and encryption. Regular updates and security checks help keep systems safe.
Training users to recognize threats reduces the risk of attacks. Backup plans ensure data recovery in case of a breach. A strong prevention strategy keeps businesses and individuals secure.
Detection

Detection helps identify cyber threats before they cause damage. It uses antivirus software, firewalls, and monitoring tools. Quick detection stops hackers from accessing sensitive data.
Regular security scans find weaknesses in systems. Alerts and logs help track unusual activities. Early detection prevents bigger security problems.
Response
Response is the action taken after detecting a cyber threat. It includes isolating infected systems and stopping further damage. A quick response helps minimize risks and protect data.
Security teams investigate the issue and fix vulnerabilities. They restore affected systems and update security measures. A strong response plan ensures fast recovery and future protection.
Also Read: What is Cloud Computing Cyber Security Fundamentals – Cybtics
Conclusion
Elements of cyber security protect data, networks, and systems from cyber threats. They include firewalls, encryption, and strong passwords. Regular updates and security checks help prevent attacks. Network security blocks hackers, while application security protects software. Disaster recovery planning ensures quick recovery after a breach. A strong cyber security strategy keeps businesses and individuals safe.